This article explains how to perform basic investigation using SECONE Threat Hunting application.
Application generates the alarms based on NetFlow (IP address reputation) and Syslog Web Proxy logs (domain/URL reputation).
This manual is for users who have registered tenant and configured network devices to send NetFlow to SEC.ONE.
The first step is to use the app and focus on critical alarms:
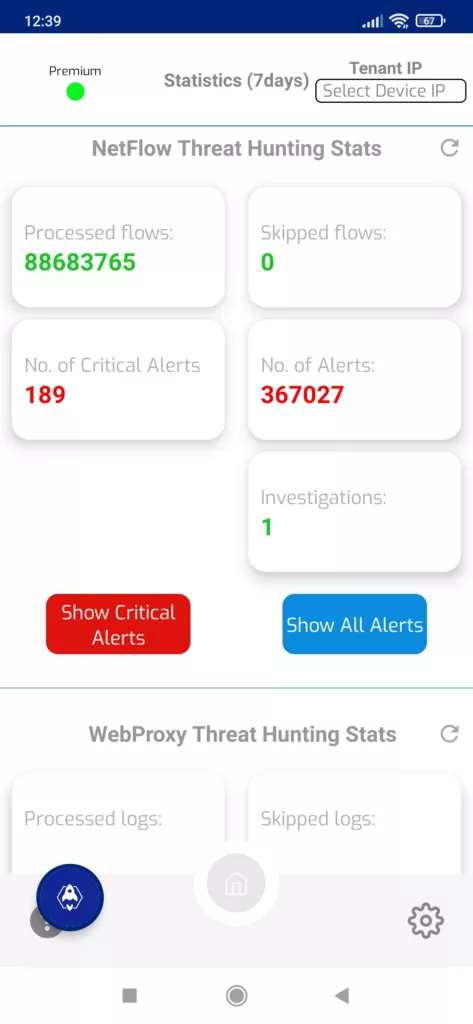
Critical alarms are the most serious one selected by our innovative Impact Selection Engine (ISE) module. It’s a dynamic engine which changes and adapts to the existing alarms / conditions / threat intel data. It’s our secret sauce. The outcome should be those most important alerts you should focus on first:
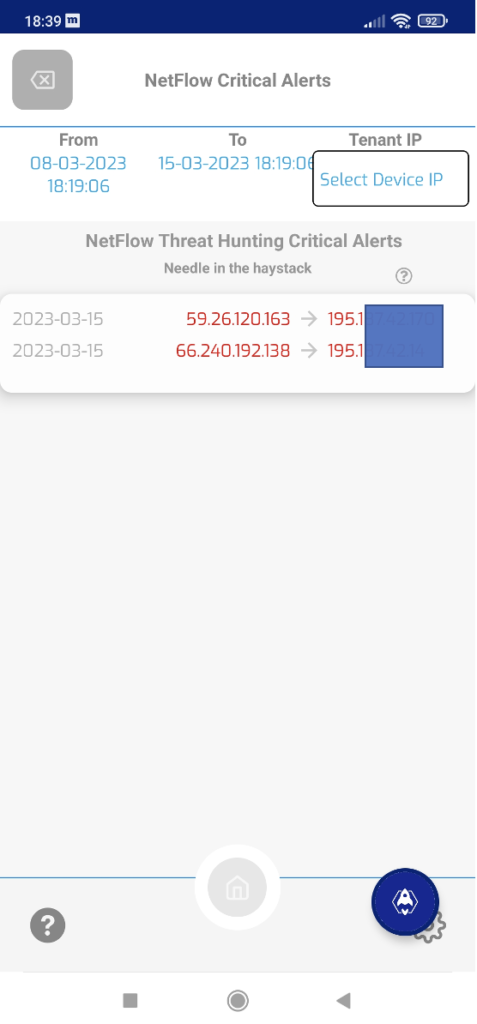
There is a connection from suspicious IP address 59.26.120.163 to the company resourcs. The next step is to check details about the associated flows:
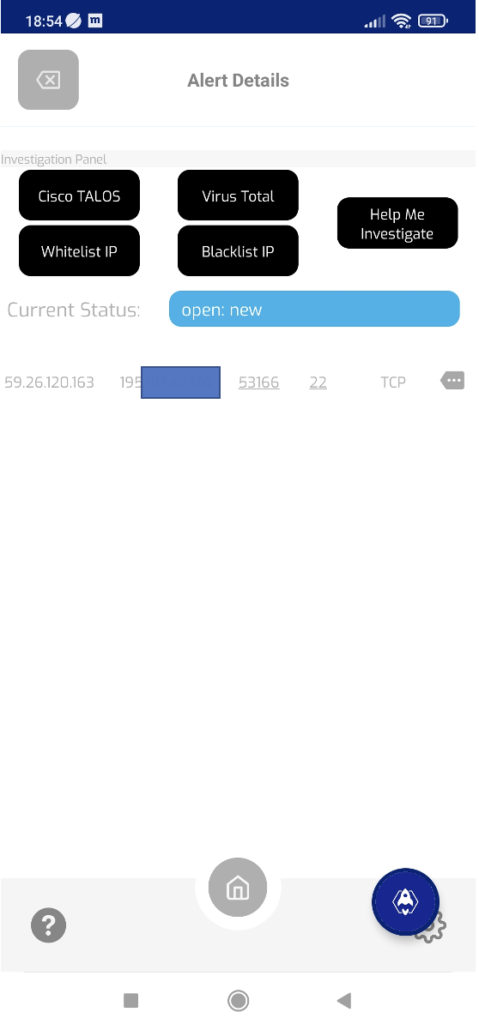
That confirms that malicious host initiated the connection to port TCP/22 only. That is probably SSH connection attempt. At this point is makes sense to confirm that it is indeed ssh via (ssh -v command connecting to that destination IP).
Our investigators do have access to underlying raw NetFlow telemetry and can check the patterns (packets/bytes and interspacing). With that it’s possible to estimate if that SSH connection was successfully authenticated or not (in case or large amount of traffic in a small time span authentication was probably succesfull).
Also by clicking right small icon additional detail could be retrieved:
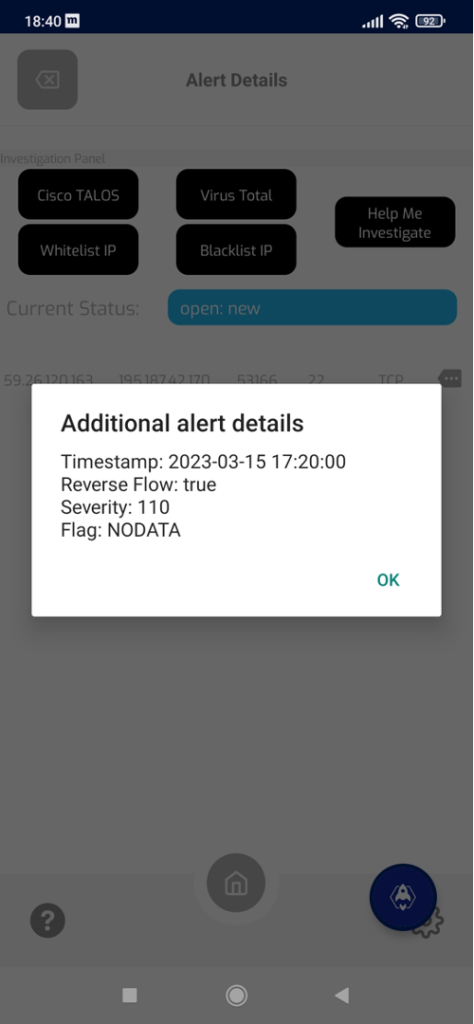
Those details reveals there is reverse flow, which means that connection was bidirectional (TCP session almost certainly established). Severity score is very high (110 in our internal database) suggesting it’s a very malicious host. Flag indicates the status for reported flow (NetFlow), NODATA means that simple NetFlow tempate was used without reporting record event (more in https://sec.one/different-types-of-netflow/)
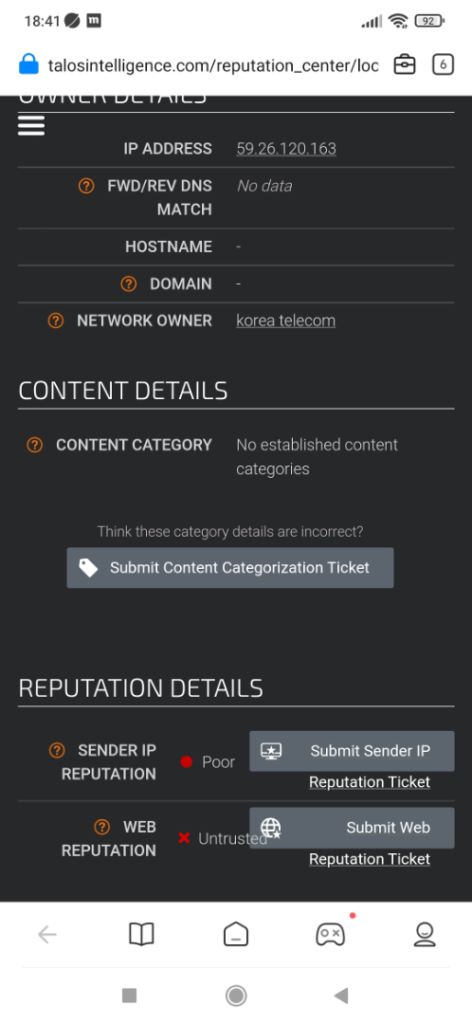
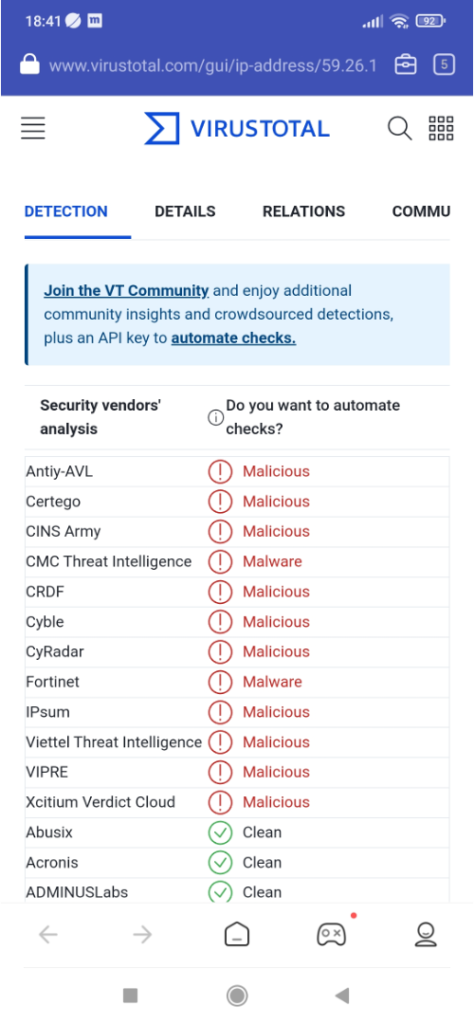
The next step would be to confirm the reputation of that IP via our links to VirusTotal and TALOS:
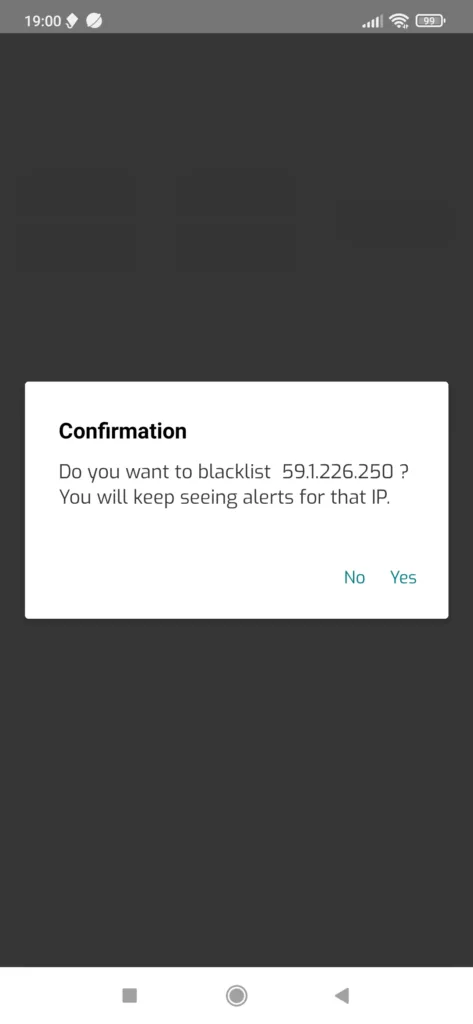
Now it’s time to make a decision. You could add that IP address to the blacklist:
And use our BGP blackholine service to automatically block communication to that IP on the border routers.
Another possibility is to open support ticket (investigation) with our team. They will investigate further, check additional details and different threat intel sources in order to undertand the attack vector, threat actor and potential impact better:
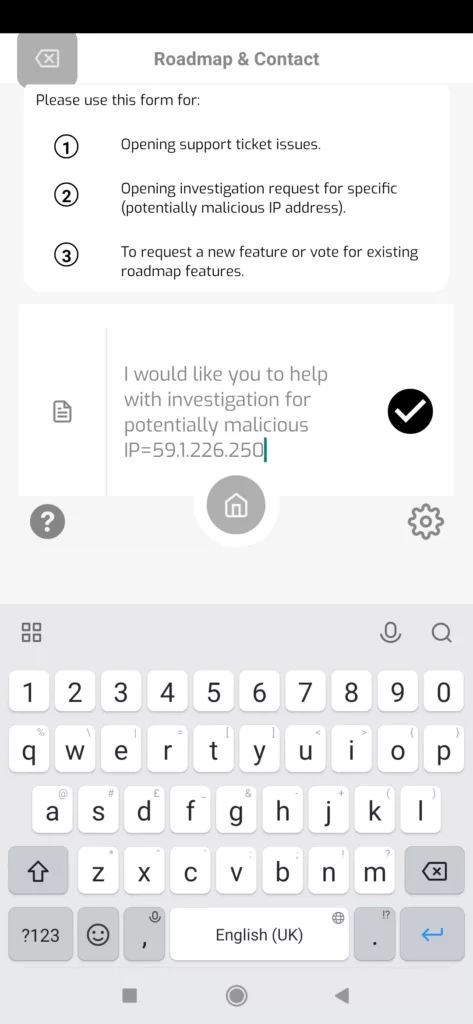
It’s always advised to activate additional telemetry sources to have more layers of defense and visibility. That would include our syslog (web proxy) telemetry analytics and also Endpoint Detection and Response (EDR) API integration.