Why we have decided to build a new solution ?
We have identified a market gap, catering to a specific niche of customers who:
- are unwilling to invest in expensive on-prem servers required for network security analytics
- prefer flexible subscription models (OPEX), with the option to cancel at any time (monthly)
- prefer transparent and straightforward costs that are easy to estimate, such as per-user licensing, rather than flow-based licensing
- require security solutions that are not vendor-restricted
- seek quick implementation times and cannot afford to wait weeks or months for protection
- prioritize their core operations and are not prepared to maintain large security teams
Despite our business-driven approach, we have expanded our technical capabilities and now offer sophisticated metadata analytics to detect threats, resulting in the development of our Impact Detection Engine (IDE). More information on IDE can be found at here.
Our values include:
- Threat detection
- Finding “needle in a haystack”
- Product time to value: 5-10 minutes
- Flexible subscription model, no CAPEX
- No hardware, no VM, no container, nor agent deployments needed
- Ideal for manufacturing, IoT, and other environments where endpoint agents cannot be installed
We do not offer:
- Reporting systems as the only value proposition for investing in security. We believe that the value lies in finding real threats
- Platforms like NDR/XDR/SOAR that prioritize data storage/processing over security and leave the responsibility of configuring rules and detecting threats to customers. Platforms are licensed based on amount of data processed – for such vendors that is the only KPI and source of revenue.
- Compliance solutions as we do not specialize in log-keeping or maintaining compliance frameworks/certifications
EDR vs NDR vs XDR vs MDR – where are we ?
EDR – Endpoint Detection and Response. We believe in endpoint-based solutions as they provide excellent visibility and protection. However, they cannot be deployed everywhere, such as on campus sensors, network devices, printers, or manufacturing environments. We are complementary to EDRs and do not replace them.
NDR – Network Detection and Response. That is our specialty!
XDR – Extended Detection and Response. These solutions usually involve platforms that aggregate different types of telemetry to provide a unified security view. However, platforms are complex to manage and require a lot of tuning and configuration to find meaningful insights. We do not offer a platform.
MDR – Managed Defense and Response. This service is typically purchased to work with a security vendor on detected threats. We offer an investigation service that allows us to work closely with customers to understand the impact and possible remediation of specific findings. This is also part of our expertise.
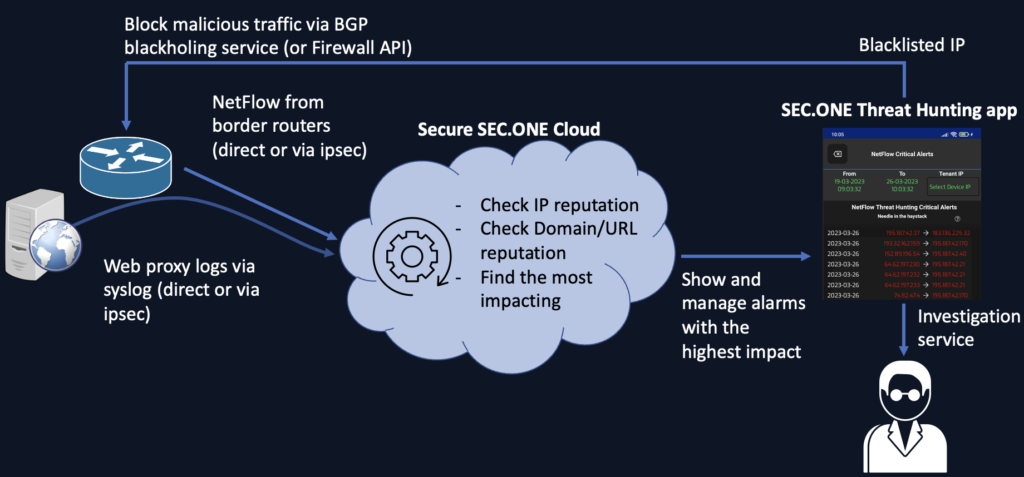
Solution Architecture
NetFlow or WebProxy (syslog) telemetry is sent to the SEC.ONE Cloud, either directly or via an IPsec tunnel. This data is then processed and the resulting outcomes are presented in the mobile application. Alerts and critical events are displayed, along with detailed information about each alert. When a decision is made, the public IP address can be added to the blacklist, which allows to block incoming traffic via BGP blackholing. Investigation service provides additional insights from our investigators and helps significantly to make the best decisions.
Partners
We offer our services directly to our customers, but we also work with partners and provide additional options for business models and technology integration. Please feel free to contact us for more information on how we can support your specific needs.