NetFlow is a protocol developed originally by Cisco Systems. It’s used to monitor and then analyze network traffic. It transports metadata about the traffic including source and destination IP addresses, ports and the protocol. Such metadata can be generated by network devices like routers, firewalls, access points or servers and send to Sec.one Cloud for security analytics. In such case for every flow the public IP address is checked for the reputation. If it’s bad (becuase associated IP address might be well known to be used for malicious purpose) the alarm is raised.
Monitoring the reputation of IP addresses for all the network traffic ingressing and egressing company premises is a first line of defence against security threats.
The most dominant version is 9 and documented in RFC3954. Supported by most network devices. It’s a flexible protocol where template configuration determines which attributes are being attached to the flows.
This article is presenting examples of NetFlow packets generated by different network devices.
Cisco Systems IOS-XE
The following template definition and flows are generated by Cisco vCSR (version 17.3) and 8000V (version 17.6) based on the configuration from here (it’s default configuration for Cisco IOS-XE)
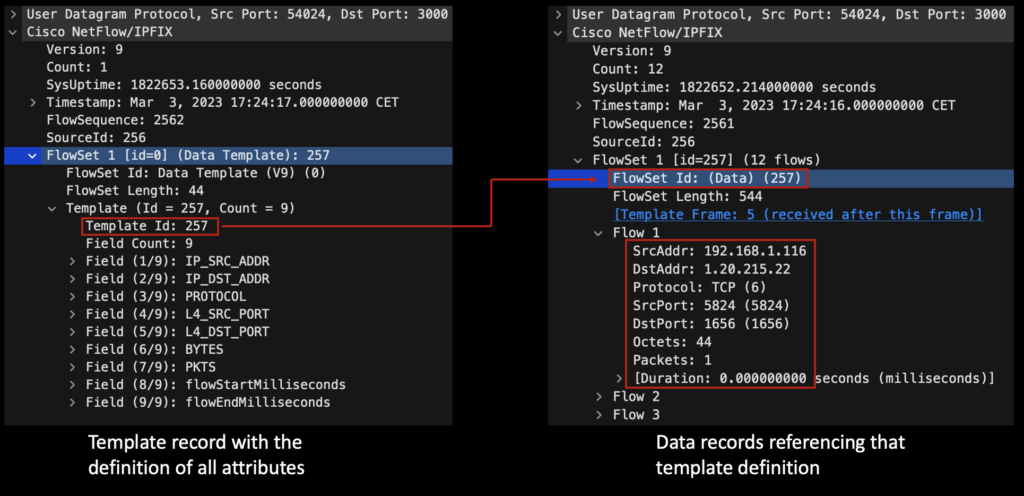
In this case it is not possible to understand if those flows were allowed or blocked, because template definition does not include such attribute. As a result when performing investigation using Threat Hunting application those flows are classified as “Allowed”. Still different network vendors/devices might behave differently. For example when having Access List (ACL) attached to the interface blocking specific traffic those denied flows might be exported or not depending on the configuration, but it’s not possible to determine that by looking at the exported flows with the default IOS-XE configuration.
Similar flows are generated by many other types of devices running IOS-XE (like 3560/3850 switches).
Cisco Systems ASA
The following template definition and flows are generated by Cisco ASA(version 9.12) based on the configuration from here (default configuration):
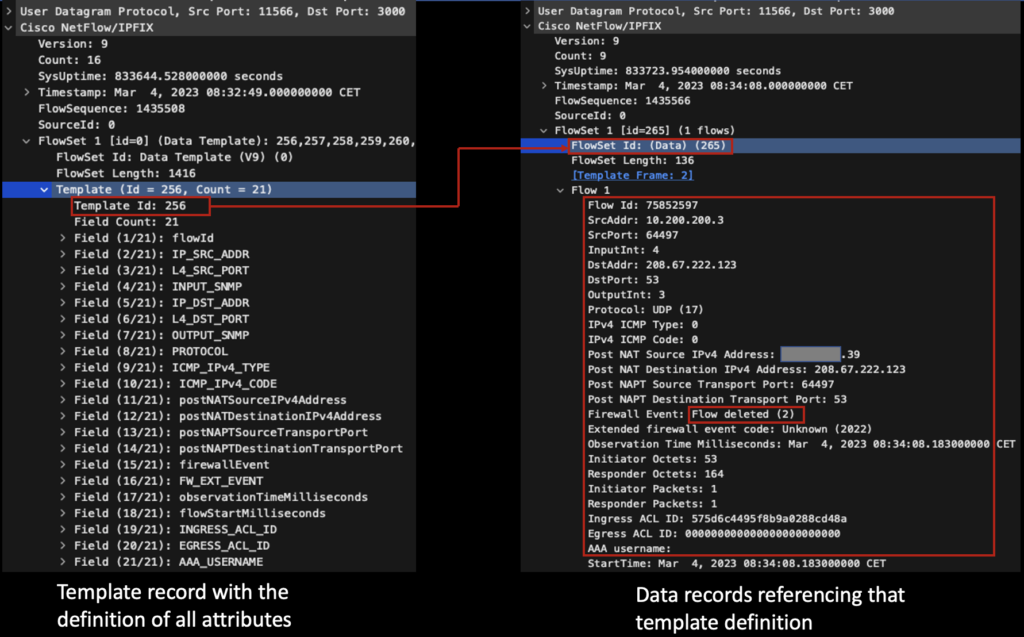
In such case the template definition and corresponding flows carry much more details. Those which are valuable for security investigation are:
-
- Firewall event: information if the flow has been created, deleted, updated or denied. Ability to differentiate denied vs allowed flows is important for investigation (events are configurable as per the following command reference)
-
- Pre and post NAT-ed IP address. Firewalls do often translate local ip addresses to a public one. Having both allows to confirm which private IP + port was associated with corresponding (potentially) malicious flow
-
- User name: if firewall is having identity services enabled the username responsible for generating that flow will be populated
Palo Alto PA
The following template definition and flows are generated by PA-220(version 10.2.3) based on the configuration from here (default configuration):
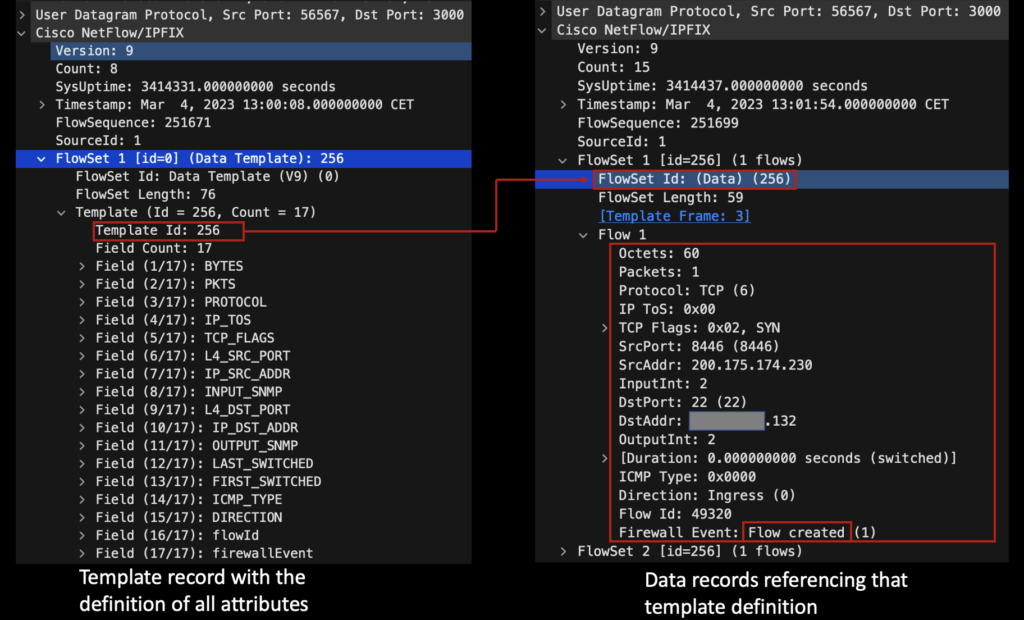
Default template configuration is more similar to ASA – allowing to differentiate blocked from allowed traffic.